So I’ve been thinking of creating a post of how to block ips when they try to do something bad to your system, for example a exploit related to a wordpress plugin on your dmz-webserver. It’s quite easy and extremely effective. Just setup a profile that will automaticly block the ip when it tries to do bad things.
So first of all, create a TAG. Name it something related to blocked-ips
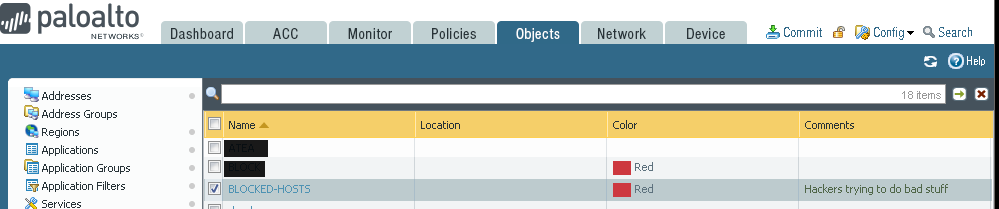
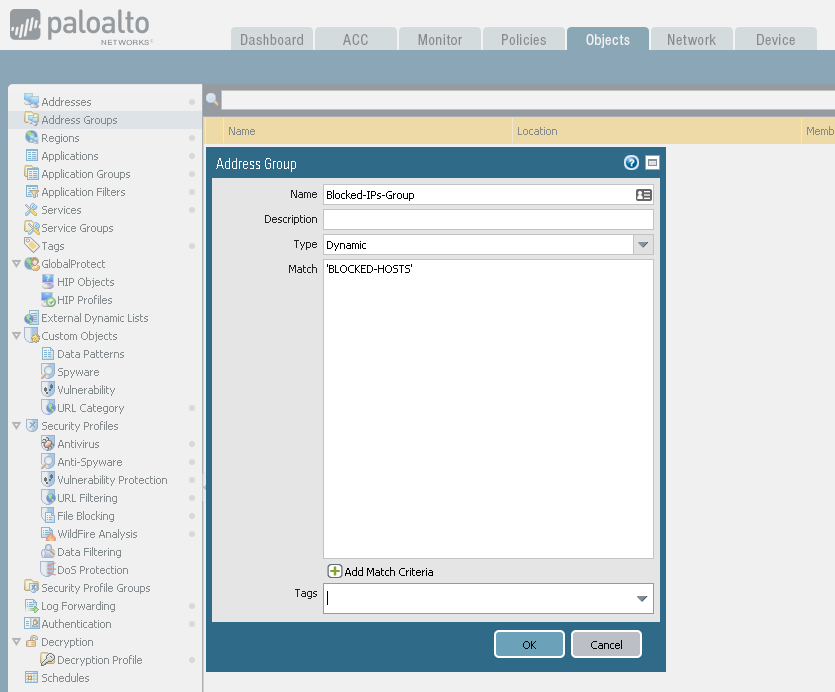
Create a Dynamic type Address Group for this TAG:
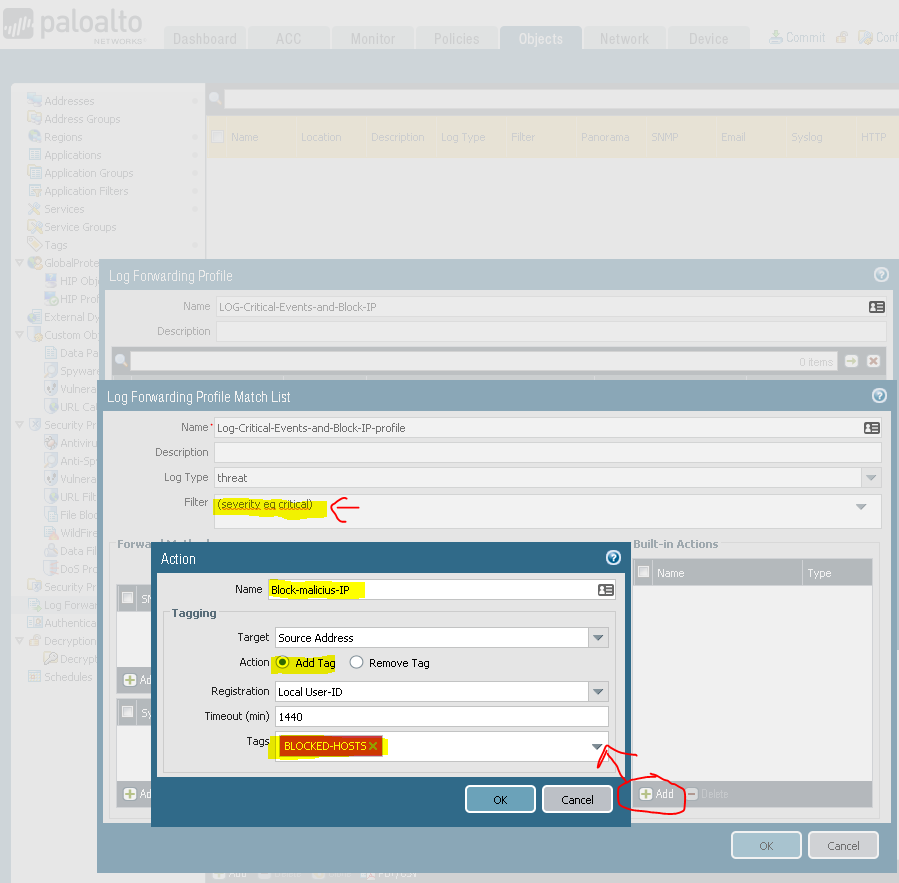
Then create a LogForwarding profile:
The result should be something like this:
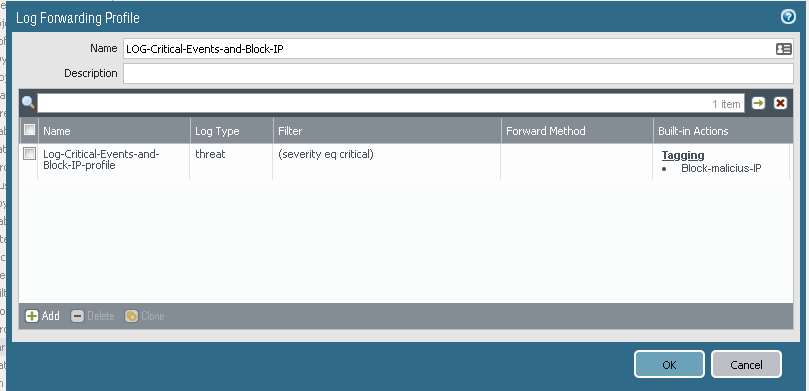
You now have a setup that matches the severity Cirtical of the logtype Threat, that adds the sourceip of the traffic-log to the BLOCKED-HOSTS tag.
Now you can use your own incomming rule and add this log-forwarding profile to it. (BE SURE that you have a threat profile active on the rule)
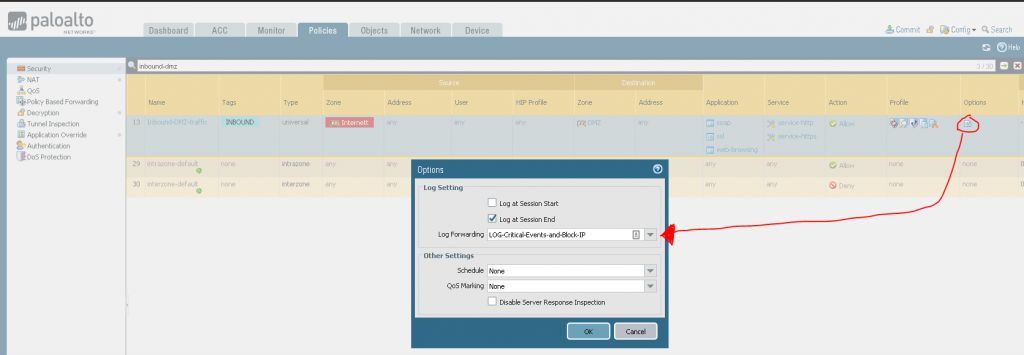
To block these IP’s you need to create a Rule above the inbound rule to block these IPs:
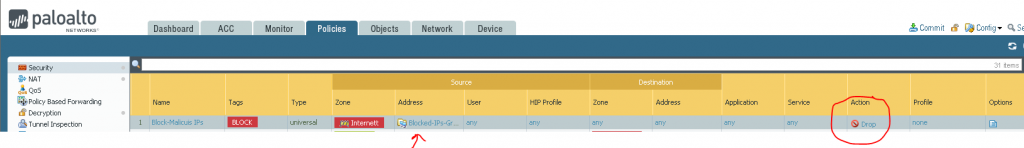
And you are good to go. Get rid of those idiots (for a selected time atleast)