The idiotic way to implement user identification when everything else fails.
You need:
GPO to push automaticly run powershell
A webserver, for example Apache
A syslog forwarder, for example rsyslog
And setup the Paloalto firewall as a User ID agent with syslog listener.
Plain and simple. Absolutely not secure, but until I bother with integrating user certificates as authentication for the requests this will do.
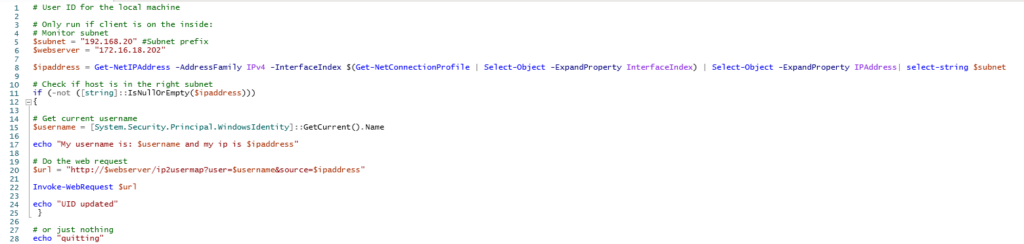
Powershell which runs every hour or minute on the clients
The webserver, a simple apache server hosted on an ubuntu box without any content
Install rsyslog if not installed
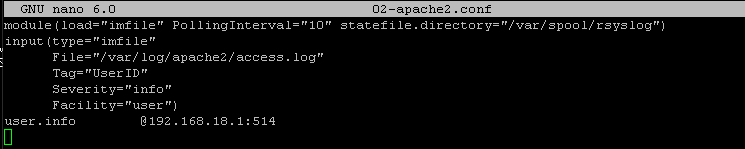
put the following in /etc/rsyslog.d/02-apache2.conf
Validate the config:
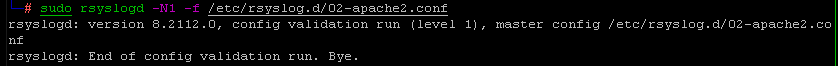
systemctl restart rsyslogd
On the paloalto, enable user-id syslog on the interface and lock the permitted address to the webserver sending the syslogs
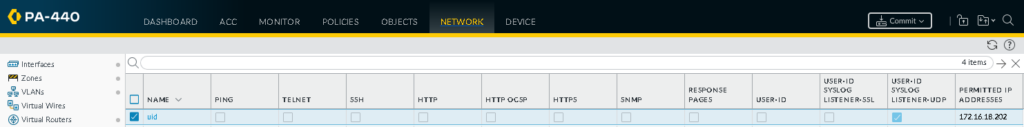
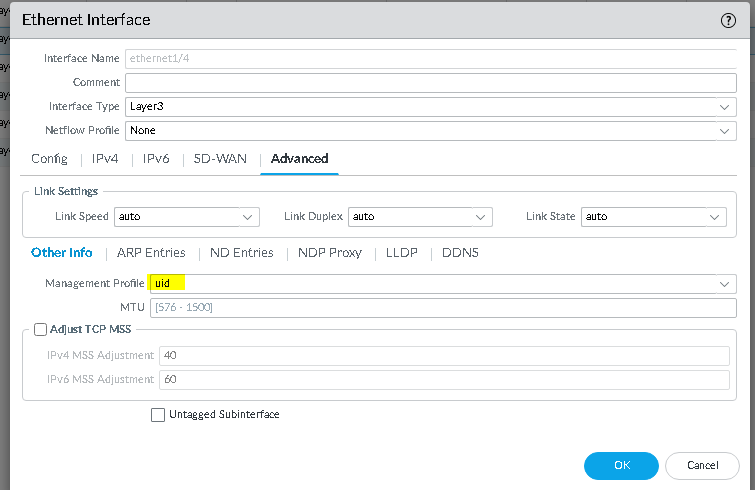
add the uid profile to the interface:
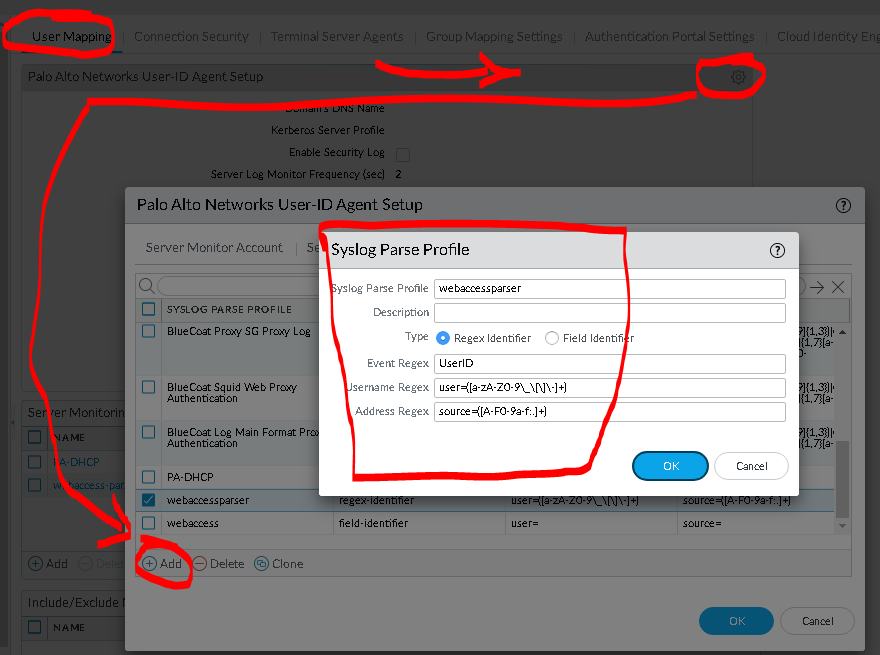
Add the following syslog parser:
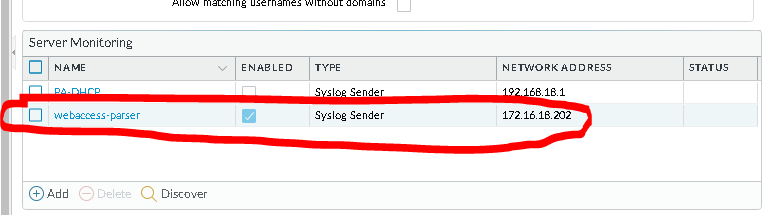
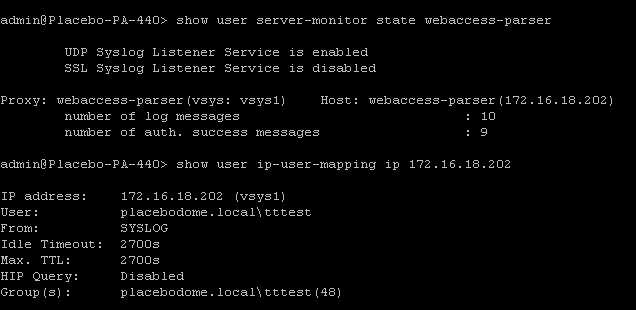
Setup the server monitor:
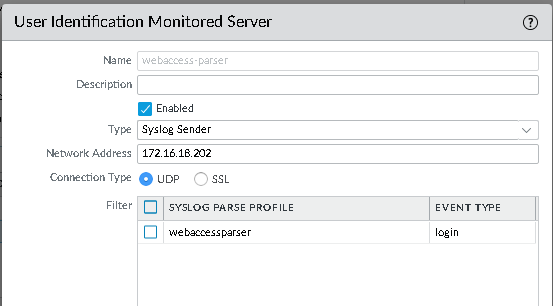
and the syslog parser profile.
And you’re good to go. Not secure, but it works as a simple solution
2 responses to “Alternative to captive webportal Palo Alto”
Hey! This is kind of off topic but I need some advice from an established blog. Is it difficult to set up your own blog? I’m not very techincal but I can figure things out pretty quick. I’m thinking about making my own but I’m not sure where to begin. Do you have any points or suggestions? Thanks
Great blog right here! Additionally your web site lots up very fast! What web host are you the use of? Can I get your associate link for your host? I desire my site loaded up as quickly as yours lol